Finding efficiency of web application firewall
Received: 22-Sep-2022, Manuscript No. PULJPAM-22-5355; Editor assigned: 26-Sep-2022, Pre QC No. PULJPAM-22-5355 (PQ); Accepted Date: Mar 27, 2023; Reviewed: 10-Oct-2022 QC No. PULJPAM-22-5355; Revised: 17-Feb-2023, Manuscript No. PULJPAM-22-5355 (R); Published: 31-Mar-2023, DOI: 10.37532/2572-8081.23.7(2).1-4
Citation: Dubba NM, Kodukula S. Finding efficiency of web application firewall. J Pure Appl Math 2023;7(2):1-4.
This open-access article is distributed under the terms of the Creative Commons Attribution Non-Commercial License (CC BY-NC) (http://creativecommons.org/licenses/by-nc/4.0/), which permits reuse, distribution and reproduction of the article, provided that the original work is properly cited and the reuse is restricted to noncommercial purposes. For commercial reuse, contact reprints@pulsus.com
Abstract
Today, with the Evolution of technology and tools like computer systems, mobiles, and tablets pieces use these http as default protocol. The fact is a huge amount of data transactions are being processed due to these the http protocol. Because of this reason http protocol is becoming a target to attackers. It is important to analyze traffic between various protocols to seek attack attempts and also take certain measures to prevent them from these attackers. In this we are going to evaluate the effectiveness of web application firewall by using confusion matrix plots we user studio as a tool for finding out the results. We focus on the precision, recall, sensitivity, accuracy and false positive rate with the help of random numbers. We used different classifiers to test the detection accuracies. The experiments show that we can also find effectiveness in a better way.
Keywords
Web application firewalls; Confusion matrix; Precision; Accuracy
Introduction
Connecting to the net has step by step turn out to be a necessity for any person residing in the virtual statistics age and as such, the contemporary platform has started developing and reworking. The new internet is interconnecting something from computer systems, telephones, and wearable gadgets to health video display units, wireless sensors, thermostats and family system.
Alongside rises a brand new era of protection challenges, requiring further emphasis on countering the risks associated with connecting extra gadgets, and detecting intrusive incidents on systems which include the increase in large scale date breaches. Detecting statistics-breaches may be done via tracking pc infrastructures using superior intrusion detection systems. This technique has been around in view that 1987 and has on account that advanced to unique branches of detection, depending on the surroundings and services to defend. Because of the rapid improvement of technology, many sports associated to every-day lifestyles are broughtto net environment; the protection of web applications (e-trade, e-authorities, e-fitness and so on.) has prolonged. Ninety two% of the internet software program web sites are uncovered to numerous assaults, and 70% of the assaults are successful Wannacry and its virus had been affecting anywhere e in the worldwide in current days. Thanks to the Internet, everywhere in the international can be attacked at any area and may incur first-rate monetary and ethical damages In the net environment attacks are intensively completed from the network layer to software program layer sections. Attackers have a tendency to the application layer due to the measures of the intrusion prevention systems on the network layer. It is seen that the assault prevention gadget in this look at executed an attack evaluation on the utility layer diploma. Application layer net packages use http shape for communique. In favoured, the assaults are based totally in this protocol. Intrusion prevention structures have made various studies on HTTP site visitors and anomalies. The most popular volunteer network concerned in this problem is the OWASP network. The maximum nowadays published popular attack strategies statistic launched via this network encompass SQL injection, damaged authentication approach, and inter-websites command execution (XSS). Attack prevention structures commonly use signature-based completely and anomaly primarily based strategies for intrusion detection systems. As an open supply, signature based totally module, MoD security is effective for regarded attacks. Another method, the anomaly based intrusion [1-5].
Materials and Methods
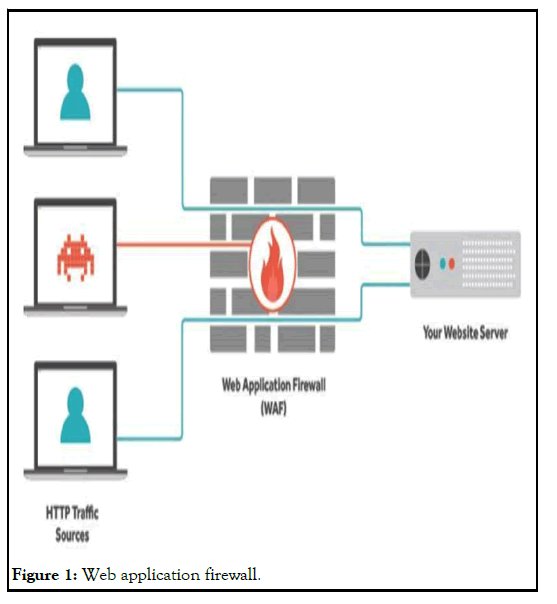
Prevention tool, makes use of a set of attributes to generate the incoming traffic. For those training they label their requests as ordinary conduct and uncommon conduct (Figure 1). The gadget must be constantly aimed towards learning new assaults [6-10].
Basic information
Selecting a template: First, confirm that you have the correct template for your paper size (Figure 2).
GeFS measure: Definitions In this subsection, we provide an outlook of the GeFS measure together with instances. The FS degree and the mRMR measure.
A GeFS degree used inside the filter version is a function GeFS(x) which has the following form with x=(x1,...,xn): GeFS(x)=a0+ni=1 Ai(x)xi b0+ni=1
Bi(x)xi, x∈0,1n In the binary values of the variable xi represents the advent (xi=1) or the absence (xi=0) of the feature fi; a0, b0 are constants; Ai(x), Bi(x)are linear capabilities of variables x1,...,xn; n is wide variety of functions. The characteristic-choice problem is to find x∈zero,1n that maximize GeFS(x).
There are several function selection measures, which may be represented by using the technique the CFS degree the mRMR measure and the Mahala Nobis distance. The mRMR function-selection measure: The proposed characteristic selection technique, that is based totally on mutual facts. In this technique, extensive capabilities and redundant functions are taken into consideration simultaneously. In terms of twin information, the significance of a feature set S for the magnificence c is defined via the average price of all twin information values between the individual function fi in S and the elegance fi∈SI (fi;c).
The redundancy of capabilities within the set S is the average fee of all mutual information values among the characteristic fi and the Features aggregate of two measures are given above and is defined as: Suppose that there are n complete set features. We use binary values of the variable xi with a view to constitute the advent (xi=1) or the absence (xi=zero) of the feature fi within the globally ultimate characteristic set. We denote the mutual statistics values I(fi;c), I(fi;fj) by constants ci, aij. Therefore, the problem can be defined as an optimization trouble as follows:
It is that the mRMR measure is an example of the GeFS measure that we denote by means of GeFS mRMR. This degree is recommended to apply while there are non-linear members of the family between functions [11-15].
CFS degree: The CFS measure assess subsets of features on the basis of the subsequent hypothesis. Good feature subsets include functions most correlated with the classification, yet uncorrelated to each other. The following equation offers the goodness of a feature subset S along with ok functions: Here, rcf is the average price of all function-classification correlations, and rff is the average price of all characteristic–function correlations. The CFS criterion may be explained as follows: By utilizing those values of the variable xi as inside the case of the mRMR degree to suggest the advent or the absence of the feature fi, we also can rewrite the assertion as an optimization hassle as follows: It is important that the CFS measure is an example of the GeFS measure. We denote this measure by means of GeFS and CFS. This is proposed to use whilst there are linear family members between capabilities. In the next subsection, we switch the optimization trouble right into a blended zero-1 linear programming trouble and show the solution to clear up it.
The proposed method and algorithms
A confusion matrix is a method for summarizing the output of a classification set of rules. A confusion matrix is a precision for estimating the outcomes of class problems. The amount of successful and inaccurate forecasts is a rectangular degree of conditional values broken down by category. This is the important part of the confusion matrix. The confusion matrix reveals how the solutions are from the predicted effects and predictions count: The variety of correct predictions for each class. The variety of incorrect predictions for each magnificence, prepared with the aid of the magnificence that become anticipated. These numbers are then they're prepared into a desk as follows: Expected down aspect: Each row of the matrix corresponds to a predicted elegance. Predicted throughout the pinnacle: Each column corresponds to a real magnificence [16].
The counts of rectangular measure of accurate and incorrect classification were then filled into the desk. For that magnificence price, the wide variety of correct predictions for a category goes into the expected row and the predicted column for that category is worth. In this way, the total scope of incorrect predictions for a group crosses into the projected line for that beauty value and the expected [17].
This matrix can be used for 2 class problems where e it is very easy to understand but can easily be applied to problems with 3 or more class values, by adding more rows and columns to the confusion matrix [18].
Recall: It is the fraction of instances of a class that were correctly predicted.
Sensitivity: It is known as the proportion of positive results that were actually positive out of the number of samples.
Accuracy: It is outlined as the proportion of elements in actual that are same with the corresponding element in predicted.
False positive rate: The false positive rate is calculated as the ratio between the number of negative events wrongly categorized as positive and the total number of actual negative events
Precision: It is defined as the correct predictions for a certain class
PR curve: Computes the area under the Precision-Recall (PR) curve for weighted and un-weighted data. In contrast to different implementations, the interpolation between points of the PR curve is done by a non-linear piecewise e function. In addition to the area under the curve, the curve itself can be obtained by setting argument curve to TRUE
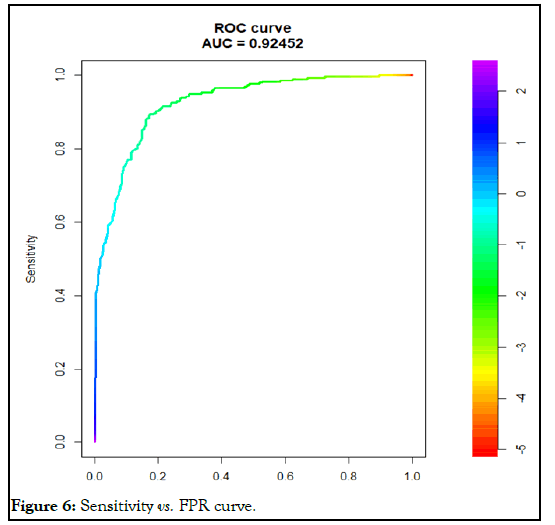
ROC curve: They are frequently used to show in a graphical way the connection between clinical sensitivity and false positive rate for a test or a combination of tests [19-24]
Results and Discussion
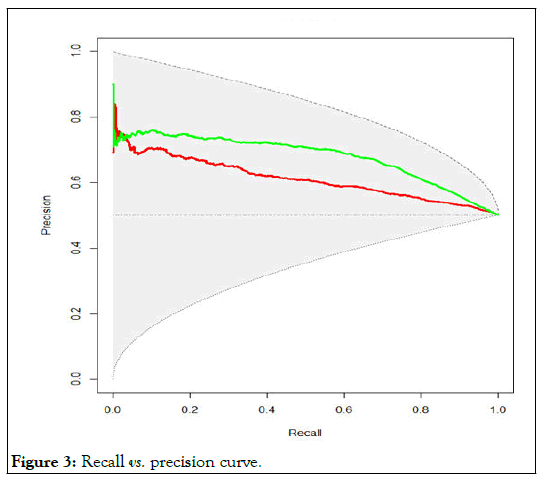
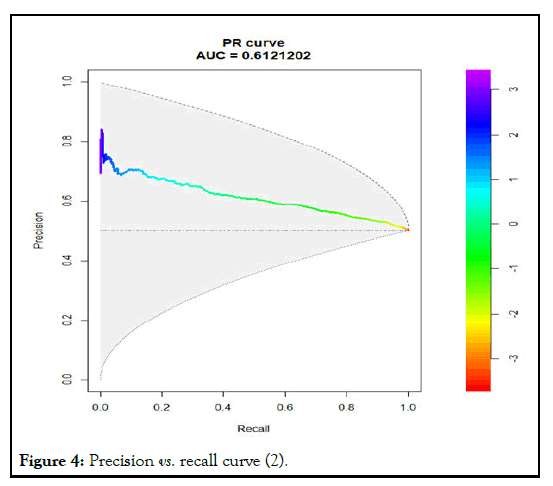
After the text edit has been completed, the paper is ready for the template. We had taken the random values to compute recall, precision, accuracy using R-tool (Figures 3-6).
Conclusion
Thereby we conclude that efficiency can be measured, and accuracy can be improved by confusion matrix, a machine learning concept using R. With the help of R studio we can have data visualization, specificity y, open source, plot graphs, and add packages.
The future work of this project can be working on real web application firewalls and finding efficiency using tools like wafbench, etc.
References
- Rakesh PA, Narasimha VB, PhaniKrishna CV, et al. A review on application security management using web application security standards. Softw Eng. 2019;477-86.
- Pradhan A, Sekhar KR, Swain G, et al. Adaptive PVD steganography using horizontal, vertical, and diagonal edges in six-pixel blocks. Secur Communon Netw. 2017.
- Prasad Rao KP, Srinivasa VP. Five phase DVR with fuzzy logic controller. J Adv Res Dynal Cont Sys. 2017.
- Alsaghier HM, Shakeel Ahamad S, Udgata SK, et al. A secure and lightweight protocol for mobile DRM based on DRM community cloud (DCC). InProceedings of the 5th International Conference on Frontiers in Intelligent Computing: Theory and Applications. 2017;475-83.
- Kruegel C, Vigna G. Anomaly detection of web-based attacks. In Proceedings of the 10th ACM conference on Computer and communications security. 2003;251-261.
- Tajpour A, Massrum M, Heydari MZ, et al. Comparison of SQL injection detection and prevention techniques. In 2010 2nd International Conference on Education Technology and Computer 2010;5(5):174.
- Mohammadi M, Chu B, Lipford HR, et al. Automatic web security unit testing: XSS vulnerability detection. In 2016 IEEE/ACM 11th International Workshop in Automation of Software Test (AST) 2016;78-84.
- Anjali DS, Rohith KK, Sai SM, et al. Breast cancer predict ion using K-nearest neighbors algorithm and R language. J Dyn Control Syst. 2018;10:92-5.
- Nguyen HT, Torrano-imenez C, Alvarez C, et al. Enhancing the effectiveness of Web Application Firewalls by generic feature selection. Logic J IPL, 2011;21(4):560-70.
- Basile C, Lio YA, Analysis of Applicat ion-Layer Filtering Policies With Application to HTTP. IEEE/ACM Transactionson Networking. 2015;23(1):28-41
- Baburao DY, Sreelakshmi K, Bora P, et al. Frequency reconfigurable dual band antenna for wireless communications. J Dyn Control Syst 2017;9(14):41.
- Tekerek A, Emci C, Bay OF, et al. Development of a Hybrid Web Applicat ion Firewall to Prevent Web Based Attacks, 2014 IEEE 8th International Conference on Application of Information and Communicat ion Technologies IEEE, Astana Kazakistan, 1-4, 15-17 Ekim, 2014.
- Girija SK, Srinivasa RK. Analysis of RF MEMS shunt capacitive switch with uniform and non-uniform meanders. Microsystem Techno logies. 2018;24(2):1309-1315.
- Kozik R. Choras M. Renk R. et al. A Proposal of Algorithmfor Web Applicat ions Cyber Attack Detection" 13th IFIP International Conference on Computer Information System s and Industrial Management (CISIM), 2014.
- Sailaja VN, Navadeep K, Mouli Ratnam KN, et al. A study on impact on european unio n with the departing countries. J Adv Res Dyn Cont Sys. 2018;10(8):210-15.
- Pawar SS, Prasanth Y. Multi-Objective Optimization Model for QoS-Enabled Web Service Selection in Service-Based Systems. New Review of Information Networking. 2017;22(1):34-53.
- Bhanu SJS, Babu AV, Trimurthy P, et al. Implementing dynamically evolvable communication with embedded systems through WEB services. Int J Electr Comput Eng Syst. 2016.
- Chandra DS, Asadi SS, Raju MVS, et al. Design of web based decision support system model study of vijayawada, A.P. Int J Civ Eng. 2016.
- Prasad AVK, Mandhala VN. Mining on social media. Web data mining and the development of knowledge-based decision support systems. 2016.
- Agarwal V, Agrawal M. Characterization and optimization of semiconductor optical amplifier for ultra-high speed applications: A Review. 2018.
- Asadi SS, Rajyalakshmi K, Kumar MS, et al. Evaluation of surface water characterist ics using remote sensing and GIS-A model study. Int J Civ Eng. 2017;8(9):1002-12.
- Rajyalakshmi U, Rao KS, Prasad SK. Integrated variable marker controlled watershed method with level sets for semisupervised classification. Int J Civ Eng. 2017;98:1-12.
- Dattatreya G, Naik KK. Circular patch on rectangular slits loaded antenna with DGS for bio medical applicantions. Int J Civ Eng. 2019;8(4):18-21.
- Banchhor C, Srinivasu N. CNB-MRF: Adapting correlative naive bayes classifier and MapReduce framework for big data classification. Int Rev Comput Softw. 2016;11(11):1007-15.